Essential Eight Assessment
Comprehensive Essential 8 Assessment to Strengthen Your Cyber Security Posture.
Essential 8 Cyber Security Assessment
The Essential 8 is a set of recommended cyber security mitigation strategies developed by the Australian Cyber Security Centre (ACSC) which is part of the Australian Signals Directorate (ASD). It is designed to help organizations protect their systems and data from cyber threats by implementing eight key security controls. These controls are not mandatory but are highly recommended to mitigate common attacks and significantly reduce the risk of cyber incidents, such as ransomware, malware, and unauthorized access.
The Essential 8 focuses on practical, cost-effective strategies that organizations can implement at various levels of maturity, ranging from Maturity Level 1 to advanced security measures at Maturity Level 3. The strategies are:
Application Control – Ensures only trusted applications are allowed to run on systems.
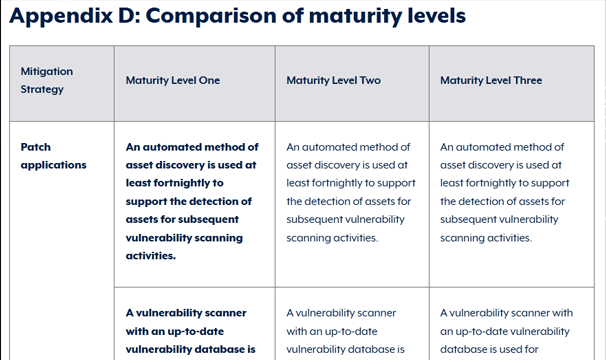
Patch Applications – Regularly apply security patches to fix vulnerabilities in software.
Configure Microsoft Office Macro Settings – Limit the use of macros to reduce the risk of malicious code execution.
User Application Hardening – Strengthen user-facing applications like web browsers and email clients to reduce attack surfaces.
Restrict Administrative Privileges – Limit access to administrative accounts to minimize potential damage from compromised accounts.
Patch Operating Systems – Ensure operating systems are up-to-date with security patches.
Multi-Factor Authentication (MFA) – Implement MFA to add an extra layer of protection for user authentication.
Regular Backups – Perform regular backups of critical data to ensure recovery in the event of a cyber attack.
Although implementing the Essential Eight Strategies may not guarantee against potential cyber attacks, it does significantly reduce the attack surface, the risk of compromise, and your resilience or ability to successfully recover from an attack.
The Essential 8 framework is also scalable and adaptable, meaning businesses of different sizes and industries can implement it at varying levels of maturity based on their specific security needs.
Refer to this link for the full Essential 8 Maturity Model - Essential Eight Maturity Model | Cyber.gov.au
Objective 1: Prevent Cyber Attacks


Objective 2: Limit the Impact of Cyber Attacks
Daily Backups
Objective 3: Data Recovery & System Availability




How can we help you?
We have the extensive cyber security experience and can significantly improve the cyber defense and threat management capabilities of all types of business and size. We have the specific Essential 8 experience to conduct a detailed and comprehensive cyber security gap assessment, and to create a tailored plan for your business to address each of the Essential 8 criteria. We also leverage our partners' strengths to bring vendor solutions as a supplement to the remediation plan as part of the road map.
We have the capability to proficiently provide your organisation with the following benefit realisation:
Implement Application Hardening and Admin Privileges Restriction to ensure that all EndPoints are aligned to World's Best Practice standards.
Ensure that the appropriate Application Control and Patching Controls are in place
Block or Restrict Microsoft Office Macro settings
Scan, Identify and Remove 3rd party applications that are unknown, non-standard and potentially dangerous.
Implement and Perform Tailored Vulnerability scans
Implement and Perform Operating Systems Patching
For all assistance in developing and implementing an Essential 8 strategy, please feel welcome to make contact via the form available HERE.
Cybersecurity Assessment
Evaluate your cybersecurity maturity based on the ASD's Essential 8 and identify vulnerabilities effectively.
Essential Eight Framework
Our assessment aligns your defenses with industry best practices, ensuring compliance with the Essential Eight framework and safeguarding your organization against evolving cyber threats.


Tailored Roadmap
Receive a customized roadmap to enhance your cybersecurity posture and achieve full compliance, protecting your business from potential cyber risks and ensuring robust defenses against threats.
Security
All Essential Eight Assessments and Remediation Road Maps are managed by EMENT.com and the affiliated team.
Compliance
Assessment
Essential8@ement.com
© 2024. All rights reserved.
