
Essential 8 Compliance
Protect your business with the Essential Eight framework and enhance your cyber security maturity effectively.
Tailored Roadmap
Achieve compliance with Essential Eight cyber security strategies effectively.
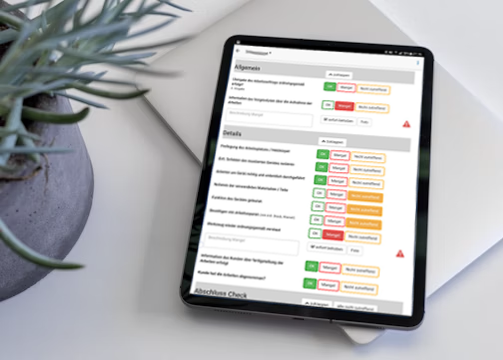

Cyber Security Assessment of Current Controls
Our Cybersecurity Assessment is the first step in aligning your organization with the Essential 8 Framework. We conduct a comprehensive review of your existing security controls, processes, and technologies to evaluate against the Maturity criteria. This assessment includes all 8 controls to determine a baseline maturity level and overall risk exposure. By benchmarking your current controls against the Essential 8 mitigation strategies, we provide you with a clear understanding of your security maturity and highlight areas that require improvement to strengthen your defenses.


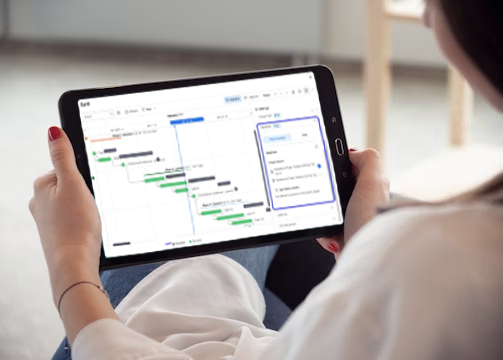


Execution of Project Plan for Compliance
Once the project plan is in place, you may choose to have our expert team manage the execution of all necessary tasks to achieve Essential 8 compliance to the desired maturity target. We coordinate and collaborate with your internal IT team to implement technical solutions, remediate identified gaps in maturity, and ensure the recommended security controls are in place. This hands-on execution phase is critical to ensuring that the strategies are applied correctly and that your organization is fully protected against emerging threats. Our process ensures that compliance is achieved efficiently and effectively.
Implementation, Remediation and Uplift Project Plan
Based on the findings from the cyber security assessment, we develop a Remediation and Uplift Project Plan tailored to your organization's specific needs. This plan prioritizes actions to address any gaps in each of the controls and the steps required to uplift these and implement the Essential 8 strategies. It includes clear timelines, resource allocation, and step-by-step guidance to bring your organization in line with industry best practices. Our approach ensures that your cybersecurity maturity is enhanced, helping you move toward full compliance while minimizing disruption to daily operations.
Ongoing Monitoring and Regular Status Reporting
Cyber security is not a one-time task—it requires continuous vigilance. Once the Essential 8 strategies are in place, we provide ongoing monitoring to track the performance of your security controls, detect potential vulnerabilities, and respond to new threats as they emerge. We also deliver regular status reports, inputs for Executive briefings and meetings offering clear insights into your organization's security posture, updates on compliance levels, and recommendations for further improvements. This ensures your business remains aligned with the Essential 8 Framework and maintains a proactive defense against evolving cyber risks.
Security
All Essential Eight Assessments and Remediation Road Maps are managed by EMENT.com and the affiliated team.
Compliance
Assessment
Essential8@ement.com
© 2024. All rights reserved.
